CA Privileged Access Manager
Protect your business and empower your people

“CA Privileged Access Manager (PAM) is a well-integrated suite that provides a comprehensive solution for privileged identity management in physical and virtual environments.”
Ivan Niccolai – Analyst | Kuppinger Cole
| FEATURES
Effectively monitor, react and record
Monitor user activity and get real-time alerts to terminate potentially damaging sessions. Recording and playback tracks all activities and events and easily archives activity to meet audit and compliance mandates.
Quickly protect your entire enterprise
Deploy as a hardened device or virtual machine to accelerate and automate your privileged access management lifecycle. Proactively control user activity to prevent policy violations, exposures and downtime.
Control access to IT resources
Centrally manage and unify privileged user policies across multiple environments. Users securely access critical IT resources without gaining a footprint on the network—while you monitor activity across the IT infrastructure.
Protect hybrid-cloud consoles
With Privileged Access Management from CA, your privileged users will gain access only to authorized hybrid cloud infrastructure — with all privileged user activity fully monitored and recorded.
Privileged User Authentication
Leverage your existing identity and access management infrastructure through integration with Active Directory, LDAP- compliant directories, RADIUS, TACACS+, smartcards, hardware tokens and more.
| COMPARE
KuppingerCole compared Privileged Access Management from CA to competitors. Check out what they found out.
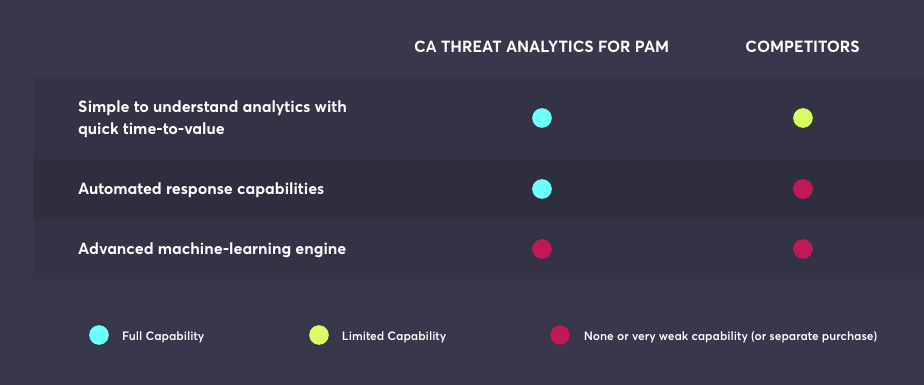
Source: KuppingerCole Report Leadership Compass: Privilege Management, Jun 2017.
CA PAM ROI Calculator
A quick way to gauge potential financial benefits of CA Privileged Access Management at your organization. Calculate your potential savings now >
| SPECS & SUPPORT
SUPPORT
COMMUNITY
Integrations
| RESOURCES
CA Privileged Access Manager Resource Center
BUYER’S GUIDE
Find a Privileged Access Management solution that’s right for you.
WHITE PAPER
Reducing the Risk of Data Breaches on Your Most Critical Servers: How CA Can Help
Protecting Your Business Amid Cybercrime’s Current Boom
Get More. Do More.

Leverage the knowledge of CA Services professionals to get more from your CA solution.

Sharpen your skills with training, certifications and resources that can transform your company and career.









